SILENT DOC Exploit 2025
Enhance Your Digital Security with Silent DOC Exploit 🔐
The exploit allows you to convert EXE to .DOC its coded 100% from scratch and used by private method to assure a great stability and lasting FUD time. You are able to attach it to the most e-mail providers nowadays everyone uses Microsoft Office so it gives a huge chance of success. Compatible with all RATs/Keyloggers/Botnets. It is advised to use FUD CRYPTER along with Silent DOC Exploit for better results.
Features :
- Unlimited Build Files
- Unlimited Spread Files
- Bypass Major AVs
- Bypass Gmail, Outlook and all other email providers
- Free Lifetime Updates
- Fully Undetectable DOC Exploit.
- Small Stub Size > 20kb
- Download and execute any file.
- Custom Template
- Private Stub
- Works with all Office Versions
- Best Customer Support 24/7.
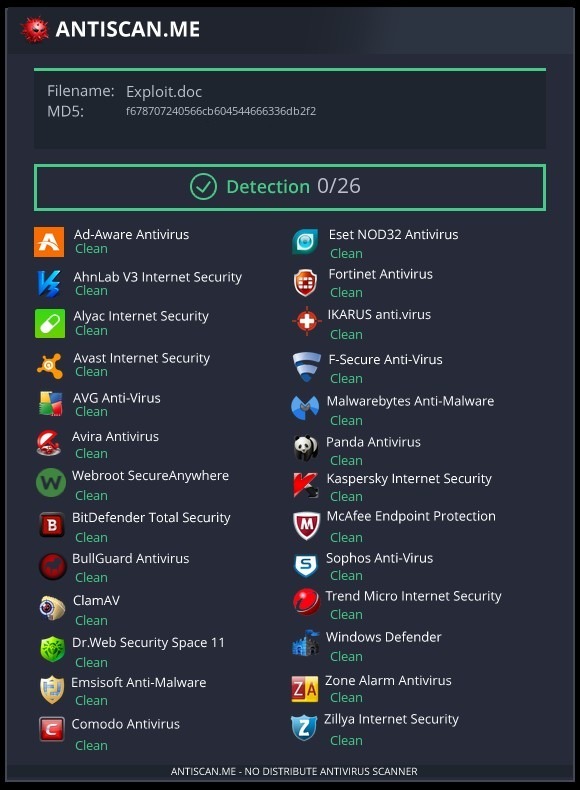
Scan Results ->
How does exploit builder work?
Exploit is a part code of software or app that uses Vuln or Vulnerability. Exploit helps hackers to use Vulnerability and bugs to gain control of a computer system or allow an intruder remotely to access a network.
Hacker using the exploit builder for the hidden malicious payload with the known format. They try hiding the malicious codes in an Exploit DOC Exploit XLS Exploit PDF Exploit office or Exploit URL.
For example, exploit builders or exploit tools already convert executable file extensions to XLS and other office extensions. It can open with any version of Microsoft Office products.
Exploit kits remain a favorite in the cyber-criminal underground. Silent exploits builder or macro exploit builders like zero-day exploits can bypass Gmail securities. In personal hacking or client hacking, exploits need to combine with social engineering tricks.
Why Silent DOC Exploit?
Because it’s the easiest way to spread. And when you send EXE file to someone they don’t simply open the file therefore you need to use .DOC Exploit for better results and achieve target penetration.



